Claude Code Internals: Intercepting Requests (MITM)
Want to see what Claude Code is doing? We'll show you how to check!
Step 1: Install mitmproxy
brew install --cask mitmproxyStep 2: Start the proxy
mitmweb --listen-host 127.0.0.1 --listen-port 58888 --web-open-browserStep 3: Set CA/TLS settings to allow interception
export NODE_EXTRA_CA_CERTS="/Users/$USER/.mitmproxy/mitmproxy-ca-cert.pem"
export NODE_TLS_REJECT_UNAUTHORIZED=0Step 4: Set proxy info
export HTTP_PROXY="http://127.0.0.1:58888"
export HTTPS_PROXY="http://127.0.0.1:58888"Step 5: Start Claude Code!
claude -p "How do I contact ai.moda?"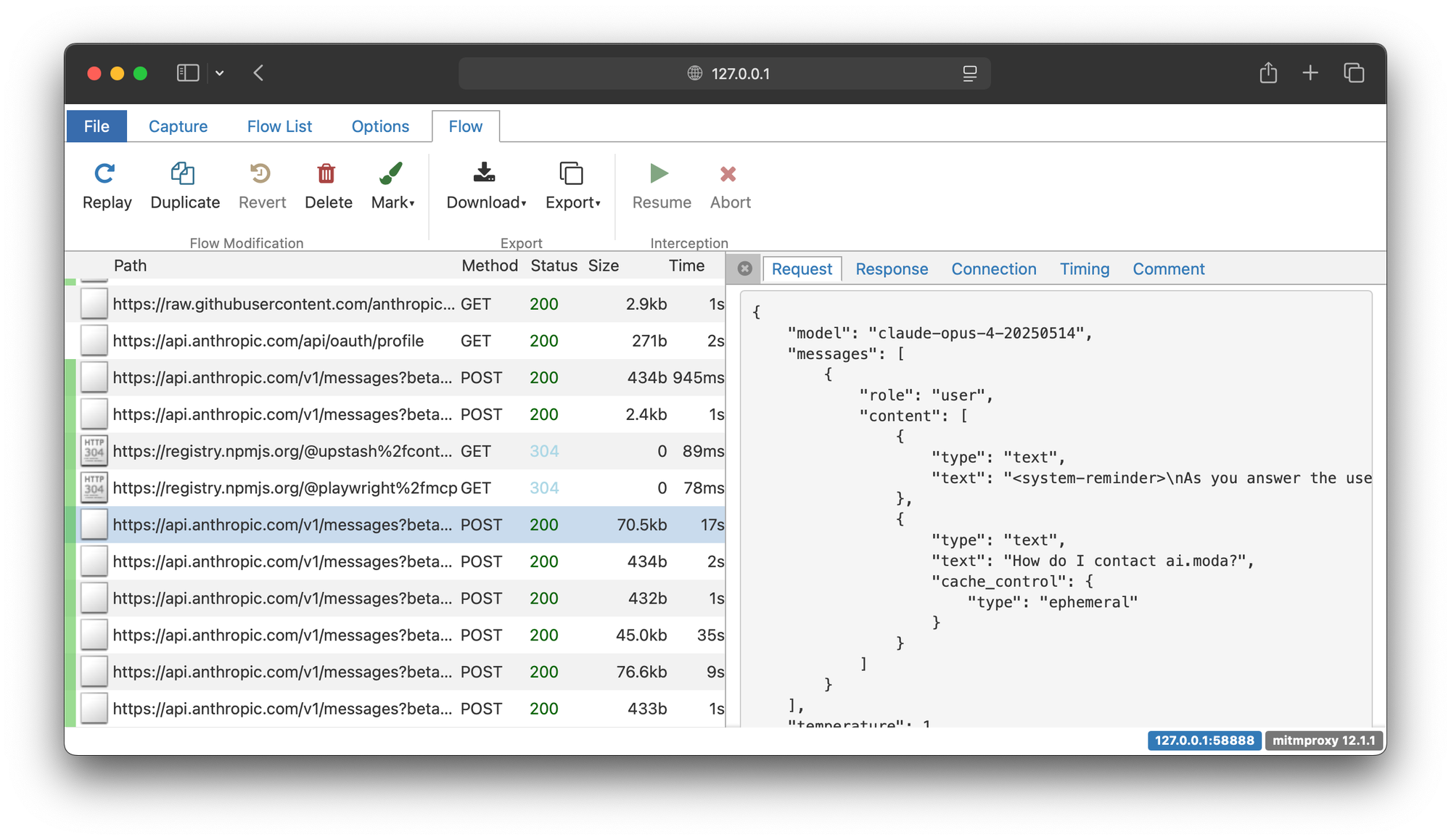
Alternative Method - Reverse Proxy
While I recommend the approach above so that you see all of the traffic (e.g. the OAuth flow, npm, etc), if you're okay with only seeing the traffic to https://api.anthropic.com/v1/messages, you can skip needing to modify Claude Code's SSL/TLS settings by using a reverse proxy.
Simply start up mitmproxy in reverse proxy.
mitmweb --listen-host 127.0.0.1 --listen-port 58888 --web-open-browser --mode reverse:https://api.anthropic.comAnd then modify your ~/.claude/settings.json to include this new ANTHROPIC_BASE_URL value.
{
"env": {
"ANTHROPIC_BASE_URL": "http://127.0.0.1:58888",
"CLAUDE_CODE_MAX_RETRIES": "1000",
"API_TIMEOUT_MS": "600000"
}
}Now, Claude Code will use your proxy for traffic to the Messages API. Unlike the HTTP_PROXY/HTTPS_PROXY method, you will not see any other traffic (like the updater checking, authorization, etc). I generally only recommend using reverse proxy mode if you are unable to configure TLS/CA settings properly in your environment.
